What is WebRTC?
Real-Time
Communications. It is an open source project for audio, video and data
transfer using javascript api. Nowadays, it is popular because it has
full support from browsers and it is easy to develop. Powered by W3C and
IETF. Today it comes embedded in browsers. In summary, it has increased
in popularity as no installation is needed, it can be developed and
open source, and it is supported by communities.
Demo: https://www.appr.tc/
For updates: https://webrtcweekly.com/
For detailed information: https://webrtc.org/
For updates: https://webrtcweekly.com/
For detailed information: https://webrtc.org/
WebRTC Leak
First, webrtc protocols to understand the weakness.
Session Traversal Utilities for NAT (STUN)
Since WebRTC exchanges data through peers, stun servers are used to provide this exchange. While providing a connection, the information sent includes our lan and wan information. Weakness in logic in the functioning of the protocol is revealed. Our ip information is not hidden, ie pure data flow between the server and the spouse is provided because our information is leaked.
Session Traversal Utilities for NAT (STUN)
Since WebRTC exchanges data through peers, stun servers are used to provide this exchange. While providing a connection, the information sent includes our lan and wan information. Weakness in logic in the functioning of the protocol is revealed. Our ip information is not hidden, ie pure data flow between the server and the spouse is provided because our information is leaked.
Traversal Using Relays around NAT (TURN)
The
difference from the Stun protocol is that it acts as a bridge in the
data flow between peers. Since the other spouse is going out of the turn
servers, our own wan and lan ip information is hidden.
Our
weakness consists of storing ip information in the request made to the
stun servers of the websites. Even if you use vpn, the ip assigned by
vpn servers will not appear because vpn protocols do not control the
information going to stun servers. In this case, whether you like triple
vpn, zenmate (which is quite unsafe but also popular) or use add-ons
like adblock, ghostery, privacy badger, the vulnerability cannot be
removed because it does not control this protocol.
Vulnerability Assessment and Solution
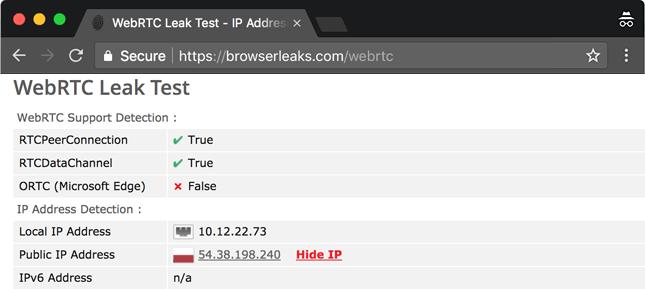
Test result with default browser settings
In the screenshot above, I used Chrome as a browser and did not take any security measures. In this case, vpn, webproxy, etc. cannot prevent leakage of this information. Pptp or openvpn connection will not be effective.
In this case, it is necessary to address the solutions according to the scanners.
In the screenshot above, I used Chrome as a browser and did not take any security measures. In this case, vpn, webproxy, etc. cannot prevent leakage of this information. Pptp or openvpn connection will not be effective.
In this case, it is necessary to address the solutions according to the scanners.
Firefox
Installing
the plugin can be solved very easily. However, it doesn’t make sense to
use the plugin when you have to adjust the browser settings. You can
find the solution with Disable WEBRTC plugin.
https://addons.mozilla.org/en-us/firefox/addon/happy-bonobo-disable-webrtc/
Enter about: config in the address line. Make sure that media.peerconnection.enabled is false. If the weakness persists, change the values below.
Enter about: config in the address line. Make sure that media.peerconnection.enabled is false. If the weakness persists, change the values below.
media.peerconnection.turn.disable = true
media.peerconnection.use_document_iceservers = false
media.peerconnection.video.enabled = false
media.peerconnection.identity.timeout = 1


